"But look what they are doing!" I said. "These are violations of
their right to vote!"
"Oh, they've always done that," he said quietly.
"You just notice it because now
they're playing games with the white folks, too. How's it feel?"
--
Bev Harris and Jerome Dudley
in
Black Box Voting:
Ballot Tampering in the 21st Century
(www.blackboxvoting.org,
Chapter 1, pages 2-3)
|
This page is an urgent call for
- the immediate release of the source code of all voting machines.
- Open voting systems
In the 2004 and 2005 Elections I used a
Diebold AccuVote-TSTM
voting machine
to cast my vote.
This page is devoted to explaining why
my and your votes on this
and other computerized voting machines
may have not counted.
Warning: HUMOR:
Bush Wins Florida!
This small humorous clip explains the problem in a nutshell.
The only difference is that when you voted,
they would be very careful to make sure that
you were not frustrated ...
User Interface.
The user interface of the
Diebold AccuVote-TSTM
is very clean.
It consists of a flat touch screen sitting on top of
a pizza-box computer. The computer has a lock
that perhaps attached it to the voting box.
One inserts a small card that supposedly loads the particular
vote ballot into the machine.
One then merely touches the appropriate squares to vote.
A final screen shows the votes.
One may back up and change votes.
(I did not try this.)
After The Vote.
After I finished voting, there was no evidence that I had voted.
As far as I could see,
my vote might not have been recorded in the machine.
My vote might have been set to anything and I could not verify
it.
My vote might be tallied later.
But there is an even worse problem.
Without open source code nobody,
not even the election officials,
knows what happened.
The Problem is in the Program.
The computers were loaded with a program.
Consider the possibility of this program, written
in Pascal.
You don't need to be a programmer to follow it.
The stuff inside "(*" and "*)" is comments to help you
see what is going on.
(* If today is November 2, 2004 then do the following ... *)
if date = "2004 November 2" then begin
(* Pick a random number between 0 and 1. *)
r := rnd(0);
(* If the random number is less than 1/100 then do the following ... *)
if r < 1/100 then begin
(* Set the vote to a Favored Candidate *)
vote := Illegally_Favored_Candidate
else begin (* other wise do this: *)
(* Set the vote based on what was pressed on the screen *)
vote := fingerpress(screen);
end
end
else begin (* When it is NOT November 2, act "normal". *)
(* Set the vote based on what was pressed on the screen *)
vote := fingerpress(screen);
end
This MADE UP snippet of code does several things.
- When the machine is tested before election day,
it will pass all validity tests with flying colors.
- ON election day,
the machine will slightly bias the vote.
A few tests might not show up anything unusual.
This is enough to throw a close election.
The bias could be much larger but it won't be detected
unless it is so large as to be wildly contradictory
to exit polls.
Even then, it would be easy for election officials
to dismiss the exit poll results as being
`unofficial'.
- If the machine is tested after election day,
it will pass all validity tests with flying colors.
How Programs Work.
To understand the severe danger that our Democracy is in,
you must understand how computer programs work.
There are two components to a program.
The first is the
source code.
The example above is source code.
It can be easily read and understood by humans.
Comments (as I gave above inside "(* ... *)" )
help but are not necessary
(or even could be misleading) to understanding
what the code does.
In some computer languages
source code can be read by the computer, but this slows
down the processing.
So in general the source code is transformed into binary.
The binary code is long strings of 1s and 0s:
10111010100110101001010011001100001101101010101
This can be read by the computer directly.
It is burned onto CDs for distribution, usually
with a severe legal warning that a user
agrees not to attempt
to convert the binary back to source code.
The Voting Computer Is a Black Box.
The use of binary means that you can not know what is going on inside
a voting machine.
Even if you had the binary of the program, you still would
still not know whether or not an
illegal code snippet like the one given above
is in the machine.
Voting officials (presumably) only get the binary
from the company,
not the source.
So the voting officials
do not really know what the program is doing and they
must trust the company.
What if the company has been paid a lot of money to
throw the election to a particular candidate?
- Without access to the source code and a means to verify that
the source code was compiled and that the binary was
used in the machine you voted with,
you cannot know whether or not the vote you cast
was recorded.
- You cannot know whether or not the vote you cast
was collected and properly tabulated.
- You cannot verify that your vote was counted as you intended.
- The election officials do not know either.
Call for Open Source Code.
There is only one way to verify the 2004 election.
The source code for all election computers must be released.
The source code must then be compiled
by election officials
and the resulting binary compared to the binary
distributed by the company.
If the comparison does not match by even one bit,
the election has been compromised!
Resources
Organizations
Blog
- 2004 Nov 3. The election is up in the air.
I started this page. It doesn't matter who officially wins.
- 2004 Nov 3. The google search for the Maryland
State Board of Elections
gave
a document that supposedly answers questions:
Marylands Better Way to Vote. Electronic Voting: Myth vs. Fact (PDF)
(Google html version).
-
Myth 1 Electronic voting systems are inherently insecure and
vulnerable to fraud.
FACTS Marylands new Direct Recording Electronic
(DRE) voting system has been studied and analyzed more than any other
voting system in use in the country. Not one of the security analyses
conducted on Marylands voting system showed evidence of fraud or
manipulation or the ability to manipulate the voting system in a polling
place, considering the procedural and human safeguards that surround an
election. The changes made as a result of the analyses improve the
security of the voting system and further diminish the likelihood of
fraud. Additionally, as noted in a recent U.S. Congressional Research
Report, there are no proven cases of tampering with the Direct Recording
Electronic (DRE) or other computer-assisted voting systems in public
elections.
The argument is invalid.
Having found no proven cases previously does not mean
tampering is not happening now.
-
Myth 2 The voting systems do not accurately record and tabulate the votes
cast.
FACTS All of the analyses of Marylands voting system confirmed that the
system counts and tabulates votes with 100% accuracy. An independent
testing authority tests the source code, a human-readable program written
by a programmer, to ensure that the software accurately records and
tabulates votes cast. Election officials and an independent verification
firm thoroughly test each voting unit to ensure accuracy.
Testing the machines on a different date from the
date of the election is invalid.
The binary code must never be supplied by the company.
The source code must must be made public to allow
anyone to verify it.
-
Myth 5 Hackers could alter a voting system by introducing a Trojan Horse
or breaking into the election management system.
FACTS A person must
have physical access to source code in order to plant a Trojan Horse
(i.e., hidden program or utility that can cause harm). Election offices
do not receive source code and only receive application software (i.e.,
computer-readable program). A person would need physical access to the
main computer to break into the election management system. This computer
is password protected and is located in a secure location. The voting
units and the main computers are never connected to the Internet.
If Election offices do not receive source code,
then who compiles the source code?
Is the compiled source code the EXACT SAME binary
as is used in the election?
- 2004 Nov 3. incorrect google:
Diebold AcuVote (one c in 'AcuVote' is wrong but this turns up
interesting material)
-
Electronic Voting Machine Information Sheet,
Diebold Election Systems -- AccuVote-TS
at
Electronic Frontier Foundation
- 2004 Nov 3. google:
Diebold AccuVote. This gives mostly official information
from the company.
- 2004 Nov 3.
E-Voting Tests Get Failing Grade, Wired (2004 Nov 1).
- 2004 Nov 3.
Group tallies more than 1,100 e-voting glitches
by Grant Gross.
- 2004 Nov 5. New links in Resources:
www.blackboxvoting.org
and
www.blackboxvoting.com
- 2004 Nov 5.
Software flaw found in Florida vote machines
by Eliot Kleinberg,
Cox News Service.
- 2004 Nov 6.
Evidence Mounts That The Vote Was Hacked
by Thom Hartmann
"Harris sat up a bit straighter, smiled, and said, "We just edited an
election, and it took us 90 seconds."
- 2004 Nov 12.
Vote Fraud Theories, Spread by Blogs, Are Quickly Buried
by TOM ZELLER Jr., the New York Times.
This article entirely misses the point that there is no way to
verify the votes many of us cast!
- 2005 Jan 4.
Senators should object to Ohio vote
by JESSE JACKSON, the Chicago Sun-Times.
- 2005 Jan 6.
Disgusting. Only ONE senator had the guts to stand up!
- 2005 Jan 11.
Can Technology Save Our Elections?
by Tamim Ansary
- 2005 Feb 5.
My experiences as an Election Judge in Baltimore County
by Avi Rubin.
Basically says what is on this page:
the voting machines are unsecure and could have been tampered with.
We cannot trust the results they give.
- 2005 Apr 5,
for 2004 Nov 11:
State settles e-voting lawsuit
by Rachel Konrad
of the
Associated Press.
Diebold Inc settled a lawsuit for
$2.6 million for selling shoddy voting equipment.
- 2005 Apr 5:
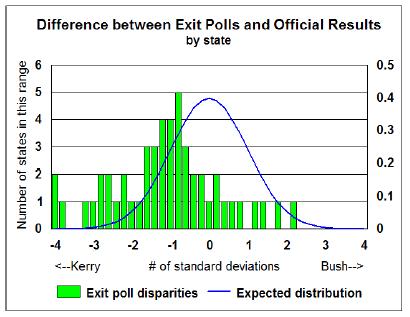
Statisticians Refute "Explanation" of Exit Polls.
The data are now quite strong that the exit polls
of the 2004 presidential election are anomalous
(see figure below).
The battle is now about why.
- 2005 Apr 16:
Write your Election Officials to Ask for Paper Ballots
- 2005 Jun 27:
US Count Votes has
a professional brochure describing
their National Election Data Archive Project
and advising how to ensure accurate election results (pdf),
from
ElectionArchive.org.
- 2005 Aug 16:
Election Fraud Continues in the US
Peter Phillips
from
Election Fraud Continues in the US
New Data Shows Widespread Vote Manipulations in 2004
"More importantly national
exit polls showed Kerry winning in 2004. However, It was only in precincts
where there were no paper trails on the voting machines that the exit polls
ended up being different from the final count. According to Dr. Steve
Freeman, a statistician at the University of Pennsylvania, the odds are 250
million to one that the exit polls were wrong by chance. In fact, where the
exit polls disagreed with the computerized outcomes the results always
favored Bush - another statistical impossibility."
- 2005 Aug 17:
Clint Curtis
"he alleged that:
At the behest of Rep. Tom Feeney, in September 2000, he was asked to write a
program for a touchscreen voting machine that would make it possible to
change the results of an election undetectably."
- 2005 Oct 23:
History of the Debate Surrounding the Validity of the 2004
Presidential Election
- 2005 Oct 31:
Math Logic Proof Shows that ESI Analysis of Ohio and National Exit Poll
Data is Bunk -- Mitofsky's Claim to "Rule Out Vote Fraud" is Proven
Incorrect
George W. Bush could have won the 2004 presidential election due to
large-scale vote fraud without election data showing the patterns that the
Election Science Institute (ESI) and pollster Warren Mitofsky claim must
exist if vote fraud had occurred. The analysis that Mitofsky presented at
the October 14, 2005 American Statistical Association fall conference has
been proven mathematically useless for testing exit poll data for vote
fraud.
- 2005 Nov:
Accountability:
Granite Bay man leads fight for open-source voting machines
Granite Bay View.
"The concept of invisible ballots created with secret software is
fundamentally flawed"
--- programmer Alan Dechert,
co-founder and president of the
Open Voting Consortium (OVC).
- 2006 Jan 17:
The Gun is Smoking - 2004 Ohio Precinct-Level Exit Poll Data Show Virtually
Irrefutable Evidence of Vote Miscount
"The National Election Data Archive (NEDA) is the first mathematical team to
release a valid scientific analysis of the precinct-level 2004 Ohio
presidential exit poll data.
NEDA's analysis provides virtually irrefutable evidence of vote miscount.
- 2006 Mar 17:
House passes paper ballot bill,
by Kelly Brewington, Baltimore Sun, March 10, 2006.
The Maryland House voted 137 to 0 to drop Diebold touch-screens!
SENATE BILL 713.
- 2006 Jun 3:
Was the 2004 Election Stolen?,
by Robert F. Kennedy Jr., Rolling Stone.
- 2006 Sep 13:
Security Analysis of the Diebold AccuVote-TS Voting Machine,
by Ariel J. Feldman, J. Alex Halderman, and Edward W. Felten
Abstract
This paper presents a fully independent security study of a
Diebold AccuVote-TS voting machine,
including its hardware and software. We
obtained the machine from a private party. Analysis of the machine, in light
of real election procedures, shows that it
is vulnerable to extremely
serious attacks.
For example,
an attacker who gets physical access to a
machine or its removable memory card for as little as one minute could
install malicious code; malicious code on a machine could steal votes
undetectably, modifying all records, logs, and counters to be consistent
with the fraudulent vote count it creates.
An attacker could also create
malicious code that spreads automatically and silently from machine to
machine during normal election activities --
a voting-machine virus.
We have
constructed working demonstrations of these attacks in our lab. Mitigating
these threats will require changes to the voting machine's hardware and
software and the adoption of more rigorous election procedures.
- 2006 Oct 26:
Diebold's secret code keeps voters in the dark,
by Mike Himowitz, Baltimore Sun
- 2006 Nov 2:
Hacking Democracy, a documentary on HBO.
"The timely, cautionary documentary HACKING DEMOCRACY exposes gaping holes in
the security of America's electronic voting system."
- 2006 Nov 2:
Guest Opinion: An urgent need for 'open-source' voting systems,
by Arthur Keller, Palo Alto online, Nov 1, 2006.
- 2006 Nov 8:
"A recount with these machines essentially involves an election official
hitting the reprint button and then saying oh the results are the same that
we already printed. All fine here, voting. This tells us nothing about
whether we have the tally. Garbage in, garbage out."
--- Avi Rubin
Washington Post
John Broder and Ian Urbina
- 2006 Nov 18:
GoTV Networks' Hack the Vote
This page was written entirely with my personal resources
on my own time.
No governmental funds, equipment,
space, time, matter or electrons were used.
Although I am a government employee,
speaking out about candidates
is allowed under
the
Hatch Act.
On page 4 of the
Pdf booklet:
"Permitted and Prohibited Activities for
Employees Who May Engage in Partisan Activity ...
May express opinions about candidates and issues".
"Expressing opinions about candidates and issues in private and in public
(even when done in a concerted way to elicit support for a candidate or
party)."
is permitted.
This page is
paid for by Thomas Schneider and not authorized by any candidate.